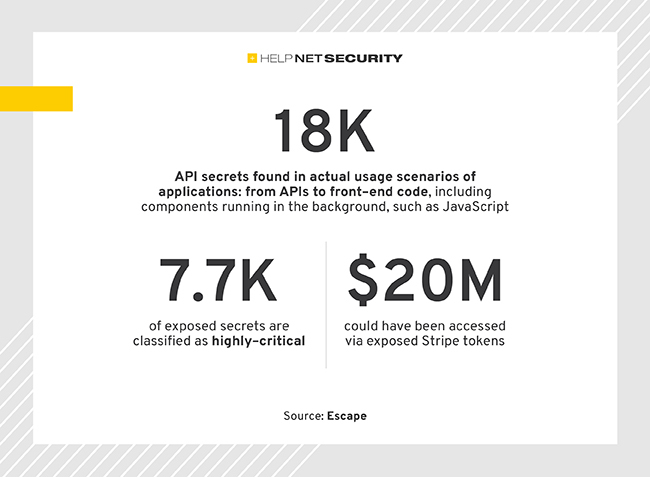
Escape’s security research team scanned 189.5 million URLs and found more than 18,000 exposed API secrets. 41% of exposed secrets were highly critical, i.e. could lead to financial risks for the organizations.
Exposed API secrets
The exposed secrets include hundreds of Stripe, GitHub/GitLab tokens, RSA private keys, OpenAI keys, AWS tokens, Twitch secret keys, cryptocurrency exchange keys, X tokens, and Slack and Discord webhooks.
GitGuardian’s ‘The State of Secret Sprawl’ indicates a 67% increase in secret sprawl in 2023 alone, with 10 million new cases of secret exposure in GitHub. This issue extends beyond GitHub, affecting all software development and operation aspects.
“Our research addresses the escalating challenge of API secret sprawl. Beyond public code, our focus extends to real-world applications, ensuring a comprehensive understanding of API vulnerabilities. The diversity of exposed secrets, from AI service keys to financial access and communication tools, emphasizes the widespread challenge of securing sensitive information,” said Tristan Kalos, CEO at Escape.
Escape’s web crawler analyzed applications in their actual usage scenarios, examining everything from APIs to frontends, including elements that run in the background like JavaScript. This approach shows how and where API secret keys and tokens are exposed in real-world settings, not only in code repositories.
How to mitigate risks
Escape researchers outlined these essential steps to mitigate risks:
- Centralize token management: By centralizing the management of tokens, you can ensure secure storage, access, and rotation. Keeping all tokens in a single location enables comprehensive monitoring of their usage.
- Rotate tokens regularly: Frequently updating tokens can lessen the impact of a potential compromise. Tools like AWS Secrets Manager can automate this process of rotating secrets.
- Allocate tokens to specific teams or services: Assign each token to designated teams or services that require it.
- Develop a revocation strategy: Implement a straightforward process for quickly revoking tokens if a security breach occurs.
- Assign appropriate permissions: Limit the permissions for each token to only what is necessary, reducing the chance of extensive damage.
- Restrict token scope: Limit each token’s access within your system.
- Monitor token usage patterns: Actively observe how tokens detect abnormal or suspicious activities.
- Train your internal teams: Make sure all team members are well-informed about the significance of token security and consistently follow established best practices.