Customer data remains a core battleground for creating unified customer experiences, especially with the growing importance of ensuring quality first-party data as businesses adjust to a third-party cookie-less world. First-party data — that which a customer voluntarily gives to a business entity — is the best source of information going forward for businesses to improve customer experiences and build trust with consumers by enabling more transparency and controls.
In 451 Research’s “Voice of the Enterprise: CXC, Consumer Trust & Privacy 2022” study, 87% of respondents are at least somewhat interested in having more control over their digital identity and how their data is used. More than 50% say the ability to opt in or out of tracking features such as cookies or location services would have a strong influence on their loyalty to a business. Transitioning to first-party data systems leaves room for data to be augmented by AI to complete the picture, meaning consumers retain the privacy level most comfortable for them while businesses can continue marketing.

Improving customer experience (CX) is one of the top drivers fueling enterprise digital transformation initiatives. These initiatives must balance the increased data volumes and risks to better understand customers. According to our “VotE: Customer Experience & Commerce (CXC), Vendor Selection 2022,” 80% of responding digitally driven leaders are focused on transforming to a real-time enterprise and unifying business data to create more contextually relevant customer experiences. As businesses become more data driven, the need to harness the power of customer data must also align with the need to manage risk, privacy and security. The business value must be to mind the gap between what security teams need to protect the organization and align both teams to the opportunity.

Setting the rules … and living with them
Businesses need to capture and unify disparate sources of customer data and effectively contextualize and operationalize information to push critical insight across channels and organizational stakeholder groups with a hand in shaping the customer journey. The changing data privacy climate between emerging regulatory requirements and consumers’ trust and privacy concerns creates a fine line to walk. This will likely put pressure on enterprises to make data privacy and security core aspects of the digital consumer experience, with transparency and control paramount in their approach to business and IT innovation. Digitally driven businesses agree that building trusted customer relationships requires investment in new tools and technologies to manage customer preferences, privacy and security. Security teams and CX-focused lines of business need further consensus to build trust, improve CX and reduce friction points.
These groups have historically conflicted over data security. Differences in motivations, technologies and metrics create problems for enterprises looking to maximize market opportunities with minimal risk. CX teams are motivated to reduce customer friction for their business lines, products or services; security teams are motivated to reduce risk or attain compliance for the entire enterprise. With the rise of software-as-a-service (SaaS) and cloud, CX teams have adopted technology independent of any centralized oversight from IT or security teams. Instead, they rely on embedded security within any application they use. By contrast, security teams choose best-of-breed data security tools to accommodate the widest variety of applications and to support all constituents throughout the enterprise. Data security motivations also contrast: CX teams liberate data access to derive more utility or insight whereas security teams default to restricting access.

CX teams have generally set the rules for the business, with security teams reacting to those initiatives. CX business lines create products and services built from customer data insight. To build these digital products and services more quickly and flexibly, business lines have historically adopted technology less dependent on any centralized oversight within IT or security teams. Equipped with an operational expense model from external cloud or SaaS platforms, business lines can theoretically build with little opportunity cost or large upfront capital expenditure. Security teams must better understand how their CX business lines are creating new business with sensitive and confidential customer data.
In response, external clouds or SaaS platforms have chosen to build security, privacy and/or compliance levels directly into their offerings. AICPA SOC 2 Type II or ISO27K compliance are now basic table stakes for SaaS or cloud-based providers. With these “shared responsibility” trust models, technology providers push data security responsibility back to the business line customer. Technology providers enable their customers to safely handle data only within that provider’s solution. Built-in encryption, data masking, authorization, or integration with identity and access management features are now common to many SaaS, platform- and infrastructure-as-a-service offerings. These built-in features enable more rapid adoption as separate security solutions do not need to be factored or layered in.
Curiously, the proliferation of data and third-party applications used by CX teams has created another cycle of disconnection. While customer data remains safe within any single platform, data’s origination and destination outside of any single system presents security challenges. Even business lines, with their customers’ data central to their products and services, may increasingly face the centralized challenge to secure customers’ data within their tools and at all places between their tools. Fittingly, individual business lines are relearning how centralized corporate security teams have serviced decentralized business lines as these individual business lines wrestle with integrating security between their third-party applications.
Business value defines opportunity of CX, security alignment
There has often been a historical perspective that security requirements for customer data are reactive, particularly in the scope of data privacy and data protection regulations. This can foster a checkbox mentality that creates friction between data security, privacy and compliance teams and the lines of business that wish to leverage data for business insight and profitability. However, today’s organizations are thinking more progressively about the proactive opportunities to align their security, privacy and CX efforts for business benefit.
Based on our “VotE: Data & Analytics, Data Governance & Privacy 2022,” enhanced customer engagement and trust are what organizations most want to achieve today in improving their data governance and data privacy efforts, reported by 41.2% of respondents. The effort to improve regulatory and legal compliance, rather than being the very top motive, comes in second place. These contemporary motives represent a fundamental shift in the way that organizations are thinking about the value of proper data stewardship as well as the downstream effects on the customer experience.
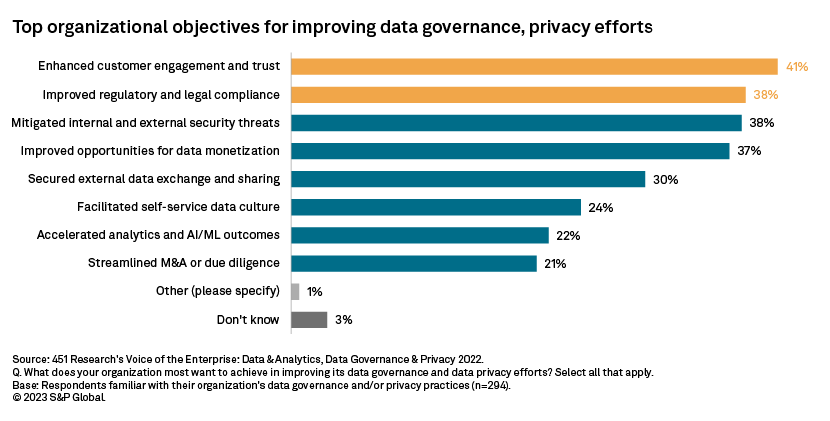
Achieving these outcomes requires alignment of objectives within the business; data security and data privacy processes and technology can no longer be at odds with functions such as marketing and analytics. The good news is that there are numerous opportunities for alignment, particularly with the increasing emphasis on first-party data. In short, first-party data tends to be high-quality data. Organizations today rarely suffer from a sheer lack of data; rather, they struggle to ensure the integrity and usability of existing data. Based on our “VotE: Data & Analytics, Data-Driven Practices 2022,” data quality and consistency is the overall top barrier organizations face in attempting to be more data driven, as reported by 35.2% of respondents. Collection of first-party data, and accompanying customer engagement, represents a direct opportunity to bolster data-quality efforts.
CX objectives for privacy and security of first-party data sources then can mesh well with data and analytics objectives for data integrity. Appropriate data use is a key element to success. Organizations need to ensure that the right people have access to the right data under the right conditions and for the right purposes. Numerous technological support options exist for this, but they differ in their approaches. Security professionals historically have preferred stand-alone or dedicated tooling for purposes such as data access governance, while marketing and CX professionals often prefer that security controls be embedded natively in the applications that they spend the most time in.
There is an argument to be made that dedicated security and governance technology can better help organizations align their business objectives around the enterprisewide leverage of data. As opposed to security controls embedded within — and exclusive to — specific applications, a dedicated security control technology can span multiple data sources and applications, allowing for enhanced consistency of data policy and governance. As organizations increasingly seek to foster data culture and cross-departmental data utilization, these mechanisms can help the business achieve the consistency of control necessary to enforce data privacy and security while allowing for more agile data utilization.
Paths forward
Looking forward, how might teams change? Perhaps the answer is a middle ground that espouses the best of both CX and security/privacy disciplines to build customer trustworthiness and loyalty. “Trust teams” have motivations, technologies and metrics that encapsulate or supersede the motivations, technologies and metrics from these previously disconnected teams. Balancing restricted or liberated data access requires optimization. Security teams have begun to decentralize, with the rise of the business information security officer role and security champion programs that advocate for and enable CX LOB to optimize data access.
The curious cycle of significant SaaS and cloud adoption among CX teams has burdened them with many different point embedded application security solutions. As CX teams continue to mature, they should consider the interoperable standards and the developer experience to build, maintain and optimize data access. While there may continue to be a desire to use embedded application security features, common interoperable security standards such as FIDO2, OAuth, OPA and KMIP may help both security and CX teams build and onboard new technologies even faster. Applications can be onboarded or relegated while leveraging existing roles, authorizations and policies-as-code. These standards better enable data interoperability and decrease applications managed in isolation while servicing customers with newer technologies in an increasingly trustworthy manner. Tech debt is reduced, and enhanced customer experiences are enabled faster.
This article was published by S&P Global Market Intelligence and not by S&P Global Ratings, which is a separately managed division of S&P Global.









