Threat actors are taking advantage of Android’s WebAPK technology to trick unsuspecting users into installing malicious web apps on Android phones that are designed to capture sensitive personal information.
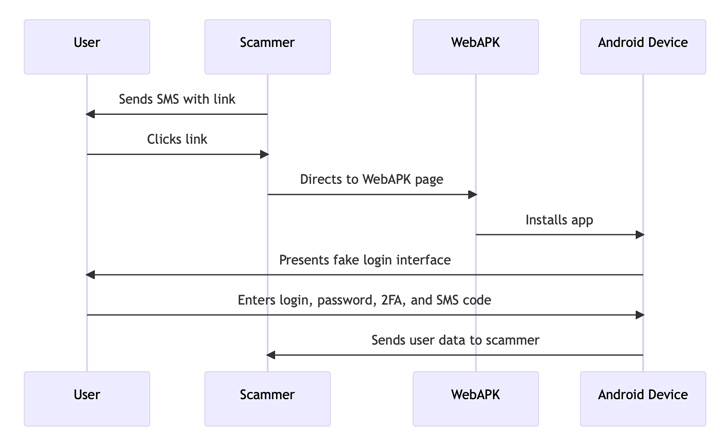
“The attack began with victims receiving SMS messages suggesting the need to update a mobile banking application,” researchers from CSIRT KNF said in an analysis released last week. “The link contained in the message led to a site that used WebAPK technology to install a malicious application on the victim’s device.”
The application impersonates PKO Bank Polski, a multinational banking and financial services company headquartered in Warsaw. Details of the campaign were first shared by Polish cybersecurity firm RIFFSEC.
WebAPK allows users to install progressive web apps (PWAs) to their home screen on Android devices without having to use the Google Play Store.
“When a user installs a PWA from Google Chrome and a WebAPK is used, the minting server “mints” (packages) and signs an APK for the PWA,” Google explains in its documentation.
“That process takes time, but when the APK is ready, the browser installs that app silently on the user’s device. Because trusted providers (Play Services or Samsung) signed the APK, the phone installs it without disabling security, as with any app coming from the store. There is no need for sideloading the app.”
Once installed, the fake banking app (“org.chromium.webapk.a798467883c056fed_v2”) urges users to enter their credentials and two-factor authentication (2FA) tokens, effectively resulting in their theft.
“One of the challenges in countering such attacks is the fact that WebAPK applications generate different package names and checksums on each device,” CSIRT KNF said. “They are dynamically built by the Chrome engine, which makes the use of this data as Indicators of Compromise (IoC) difficult.”
Shield Against Insider Threats: Master SaaS Security Posture Management
Worried about insider threats? We’ve got you covered! Join this webinar to explore practical strategies and the secrets of proactive security with SaaS Security Posture Management.
To counter such threats, it’s recommended to block websites that use the WebAPK mechanism to carry out phishing attacks.
The development comes as Resecurity revealed that cybercriminals are increasingly leveraging specialized device spoofing tools for Android that are marketed on the dark web in a bid to impersonate compromised account holders and bypass anti-fraud controls.
The antidetect tools, including Enclave Service and MacFly, are capable of spoofing mobile device fingerprints and other software and network parameters that are analyzed by anti-fraud systems, with threat actors also leveraging weak fraud controls to conduct unauthorized transactions via smartphones using banking malware such as TimpDoor and Clientor.
“Cybercriminals use these tools to access compromised accounts and impersonate legitimate customers by exploiting stolen cookie files, impersonating hyper-granular device identifiers, and utilizing fraud victims’ unique network settings,” the cybersecurity company said.