Mandiant attributed the recent exploitation of a zero-day vulnerability in Barracuda’s Email Security Gateway appliances to an espionage actor supporting the Chinese government.
In a blog post Thursday, Mandiant provided additional information about an ongoing investigation into exploitation of a zero-day vulnerability, tracked as CVE-2023-2868, in Barracuda ESG appliances that was disclosed last month. Based on several infrastructure and malware code overlaps, Mandiant assessed with high confidence that the Chinese nation-state actor it named “UNC4841” is behind what it attributed as cyberespionage attacks.
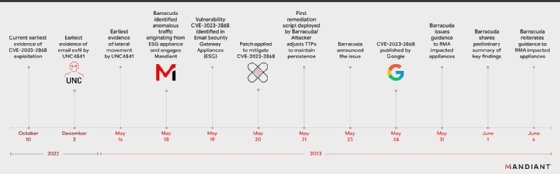
While Mandiant confirmed that exploitation of CVE-2023-2868 began as early as October, the investigation determined that UNC4841 threat actors were most active between May 22 and May 24 and targeted “a number of victims located in at least 16 different countries.”
“Overall, Mandiant identified that this campaign has impacted organizations across the public and private sectors worldwide, with almost a third being government agencies,” Mandiant wrote in the blog post.
Mandiant’s report also shed light on why the two patches Barracuda released last month were insufficient, forcing the vendor to advise customers to replace compromised ESG appliances. An initial patch was available on May 20, followed by an additional fix on May 21, but the threat actor responded swiftly with changes to its custom malware.
Mandiant said that between May 21 and 23, “UNC4841 quickly made modifications to both SEASPY and SALTWATER related components in order to prevent effective patching.” Seaspy and Saltwater were two of the three malware code families Mandiant observed during the attacks, along with a third family called Seaside. Threat actors leveraged the three to “masquerade as legitimate Barracuda ESG modules or services.”
Austin Larsen, senior incident response consultant at Mandiant, part of Google Cloud, expanded on the patch issues in an email to TechTarget Editorial. UNC4841 was able to retain access regardless of patches and firmware updates because it is a fairly sophisticated and aggressive threat actor, he said.
“In response to Barracuda’s initial remediation actions, UNC4841 displayed an interest in and commitment to maintaining persistent access to the subset of compromised appliances. Due to the sophistication displayed by UNC4841 and lack of full visibility into all compromised appliances, Barracuda has elected to replace and not reimage the appliance from the recovery partition out of an abundance of caution,” Larsen said.
One way threat actors maintained persistence, according to the blog, was executing Seaspy by inserting a command into the update_version Perl script executed by the appliance. Larsen attributed UNC4841’s ability to modify the script to the access it gained through the successful exploitation of CVE-2023-2868. He added that Mandiant and Barracuda have not identified successful exploitation of CVE-2023-2868 since the release of the May 20 patch.
Another way threat actors maintained persistence and circumvented the patching efforts started with the reverse shells they established by using domains rather than IP addresses. Subsequently, they leveraged the reverse shells through hourly and daily cron jobs on compromised devices. Mandiant also observed UNC4841 deploying a kernel rootkit it dubbed “Sandbar,” which executed during devices’ startup.
TechTarget Editorial also contacted Barracuda for additional insight into why the patches and firmware updates were ineffective. The vendor provided a statement similar to previous ones, with one addition.
“Barracuda partnered closely with Mandiant and its government partners to investigate the exploit behavior and malware. Mandiant identified the suspected China-nexus actor, currently tracked as UNC4841, and assesses with high confidence that the group is working in support of the People’s Republic of China,” the statement read.
Attacks spanning 6 months
Mandiant provided a detailed timeline of the Barracuda ESG attacks that showed UNC4841 began a phishing campaign against victim organizations as early as Oct. 10. Those emails contained clear signs of spam, such as the use of poor grammar, a red flag emphasized in security awareness training programs. Mandiant, however, believes that tactic was purposeful.
“Mandiant assesses UNC4841 likely crafted the body and subject of the message to appear as generic spam in order to be flagged by spam filters or dissuade security analysts from performing a full investigation. Mandiant has observed this tactic utilized by advanced groups exploiting zero-day vulnerabilities in the past,” the blog post read.
According to Mandiant’s timeline, the first successful email exfiltration attempt was on Dec. 10, but it would still be months before Barracuda became aware.
After the initial compromise, Mandiant and Barracuda observed two notable factors. First, threat actors aggressively targeted data of interest for exfiltration. Second, they deployed additional tooling to maintain persistence, such as the malware containing backdoors known as Seaspy, Seaside and Saltwater.
The first sign of UNC4841 conducting lateral movement inside organizations was on May 16, and Barracuda first identified malicious activity on ESG appliances two days later. The remote code injection vulnerability was assigned a CVE ID on May 19 with a patch applied the following day. Barracuda issued an additional remediation script on May 21, but the threat actor adjusted its tactics, techniques and procedures on the same day in response to the fixes.
After the initial advisory on May 24, Barracuda published additional guidance for affected ESG appliances on May 31 advising customers to “discontinue” the use of compromised appliances.
Barracuda updated the advisory with an action notice on June 6 that rang with increased urgency. “Compromised ESG appliances must be immediately replaced regardless of patch version level,” the update said. Barracuda later issued a statement to TechTarget Editorial that said the vendor would be “providing the replacement product to impacted customers at no cost.”
Although the zero-day vulnerability was exploited months prior to discovery and available patches, only 5% of active ESG appliances worldwide have been affected as of June 10, according to Barracuda.
Mandiant applauded Barracuda for its response to the ongoing situation. Like Barracuda, Mandiant urged users to replace all compromised appliances. In addition, Mandiant’s blog post advised all affected organizations to search for indicators of compromise provided by both vendors, review email logs and revoke affected credentials.
Arielle Waldman is a Boston-based reporter covering enterprise security news.









