The Iranian threat actor tracked as APT34 has been linked to a new phishing attack that leads to the deployment of a variant of a backdoor called SideTwist.
“APT34 has a high level of attack technology, can design different intrusion methods for different types of targets, and has supply chain attack capability,” NSFOCUS Security Labs said in a report published last week.
APT34, also known by the names Cobalt Gypsy, Hazel Sandstorm (formerly Europium), Helix Kitten, and OilRig, has a track record of targeting telecommunications, government, defense, oil and financial services verticals in the Middle East since at least 2014 via spear-phishing lures that culminate in the deployment of various backdoors.

One of the key traits of the hacking outfit is its ability to create new and updated tools to minimize the odds of detection and gain a foothold on compromised hosts for extended periods of time.
SideTwist was first documented as used by APT34 in April 2021, with Check Point describing it as an implant capable of file download/upload and command execution.
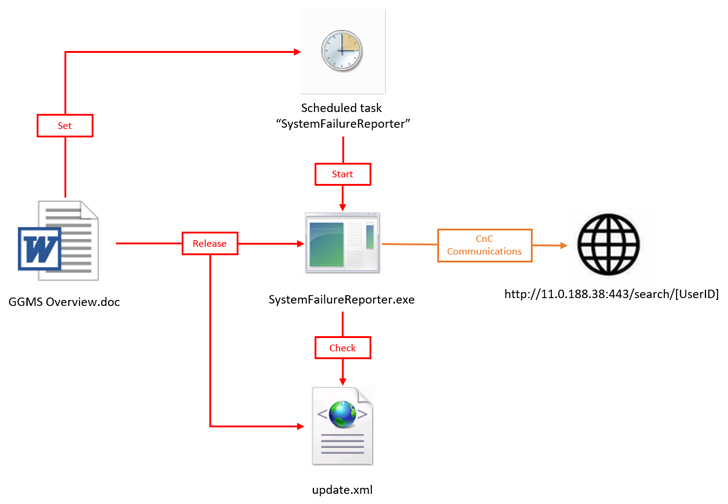
The attack chain identified by NSFOCUS starts with a bait Microsoft Word document that embeds within a malicious macro, which, in turn, extracts and launches the Base64-encoded payload stored in the file.
The payload is a variant of SideTwist that’s compiled using GCC and establishes communication with a remote server (11.0.188[.]38) to receive further commands.
The development comes as Fortinet FortiGuard Labs captured a phishing campaign that spreads a new Agent Tesla variant using a specially crafted Microsoft Excel document that exploits CVE-2017-11882, a six-year-old memory corruption vulnerability in Microsoft Office’s Equation Editor, and CVE-2018-0802.
Way Too Vulnerable: Uncovering the State of the Identity Attack Surface
Achieved MFA? PAM? Service account protection? Find out how well-equipped your organization truly is against identity threats
“The Agent Tesla core module collects sensitive information from the victim’s device,” security researcher Xiaopeng Zhang said. “This information includes the saved credentials of some software, the victim’s keylogging information, and screenshots.”
According to data shared by cybersecurity firm Qualys, CVE-2017-11882 remains one of the most favored flaws to date, exploited by “467 malware, 53 threat actors, and 14 ransomware” as recently as August 31, 2023.
It also follows the discovery of another phishing attack that has been found to employ ISO image file lures to launch malware strains such as Agent Tesla, LimeRAT, and Remcos RAT on infected hosts.